In 2010, cyber-criminals created and distributed one-third of all existing viruses, creating 34 percent of all malware that has ever existed, according to PandaLabs annual security report.
PandaLabs did find the speed at which the number of new threats grew has actually decreased compared to 2009. Every year since 2003, new threats grew by at least 100 percent, but in 2010, the increase was 50 percent.
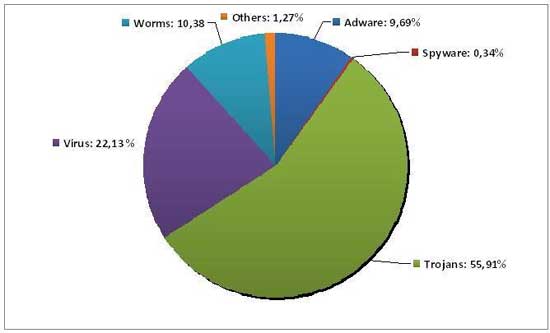
Banker Trojans topped the ranking of new malware that appeared in 2010 (56% of all samples, followed by viruses and worms. Rogueware (fake antivirus software) already comprised 11.6 of all the malware gathered, and has become a category, that despite appearing only four years ago, has created chaos among users.
The countries leading the list of most infections are Thailand, China and Taiwan, with 60 to 70 percent of infected computers.
2010 witnessed hackers exploit social media, the positioning of fake websites and zero-day vulnerabilities as its primary methods of infection. Spam also kept its position as one of the main threats in 2010, despite the fact that the dismantling of certain botnets (like the famous Operation Mariposa or Bredolab) prevented many computers from being used as zombies to send spam. This created a positive effect in spam traffic worldwide. Last year, approximately 95 percent of all email traffic globally was spam, but this dropped to an average of 85 percent in 2010.
The report also found the most important security incidents affecting the most popular social networking sites. Facebook and Twitter were the most affected, but there were also attacks on other sites including LinkedIn and Fotolog. There were several techniques used for tricking users on these sites, such as hijacking Facebook’s "Like" button, stealing identities to send out messages from trusted sources, exploiting vulnerabilities in Twitter to run Javascript code and distributing fake apps that redirect users to infected sites.







 WebProNews is an iEntry Publication
WebProNews is an iEntry Publication