The global burden of cyberattacks has become increasingly heavy for American businesses. 2023 saw a 20% increase compared to 2022, with a large percentage directed at healthcare organizations such as hospitals and cancer clinics.
With one cyber attack occurring every 39 seconds, US healthcare organizations are progressively more at risk for ransomware, breaches, and DNS attacks.
So what does the industry need today to avoid complex outages tomorrow?
To answer this question, let’s reflect on the healthcare industry’s most substantial cyber attacks, including the most recent – Change Healthcare cyber attack.
1. Change Healthcare Cyber Attack: February 2024
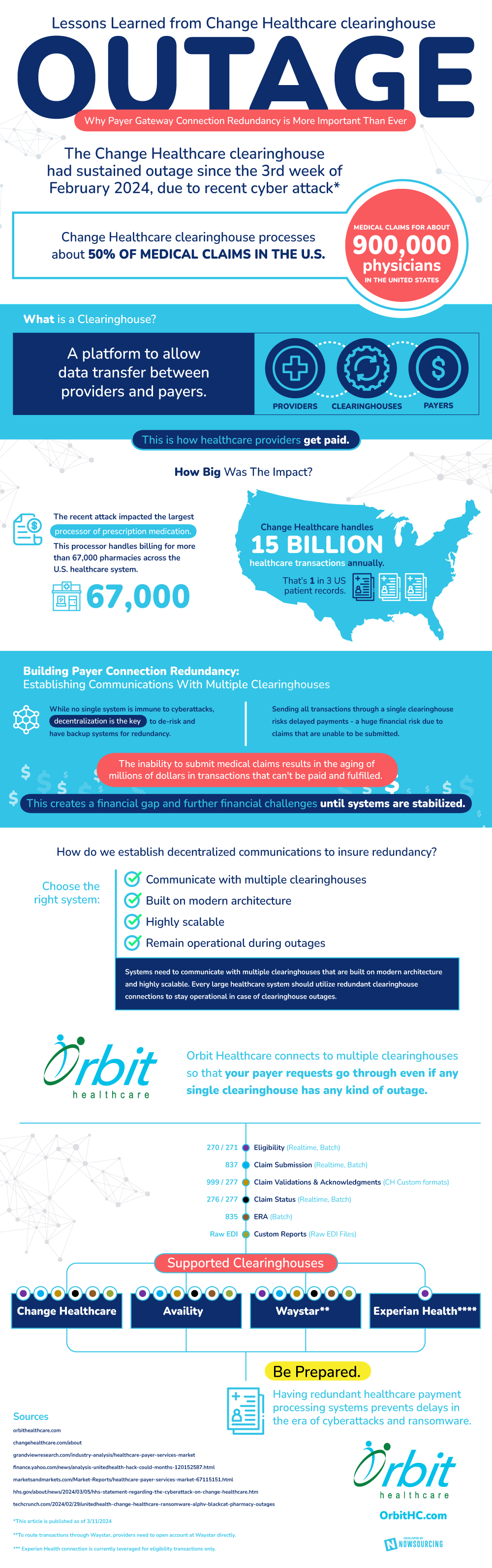
The Change Healthcare clearinghouse experienced a systemwide outage after a ransomware attack shut down America’s largest healthcare payment system. Company-wide disruption affected millions of patients and physicians, with thousands of healthcare clinics unable to submit insurance claims for processing.
The company expects to restore claims functionality as of March 15, 2024. However, its ripple effect on both patients and providers has left a lasting impact on the industry at large.
The takeaway: Redundancy is key to navigating the dangerous new world of ransomware. Decentralized communications ensure flexibility and survivability even during clearinghouse outages.
2. OneTouchPoint (OTP): July 2022
OneTouchPoint, a printing vendor serving healthcare organizations, discovered locked and encrypted files in July 2022. A few weeks later in early August, more than 30 OTP clients (all of which were healthcare and insurance providers) announced breaches connected with the stolen data.
More than 2.6 million people were affected by the OTP data breach, which included personal identifiable information such as SSI numbers and employee IDs. OTP was placed under investigation and faced multiple lawsuits for the neglect of sensitive data.
The takeaway: Healthcare organizations should perform annual security reviews to look for gaps in their defenses and potential vulnerabilities. They should also encourage their vendors to provide annual security reports so stakeholders can make informed decisions.
3. TRICARE Data Breach: September 2011
Although the TRICARE data breach occurred more than a decade ago, it was perhaps the most notable security incident recorded in 2011. For those unfamiliar, a briefcase containing backups of EHRs was discovered missing after an employee’s vehicle was vandalized.
Although investigators couldn’t determine whether the thieves understood what they stole, the company decided to treat the loss as a data breach. Complicating the situation was an insufficient encryption method — it did not align with federal standards.
The takeaway: Upgrading data retention policies could be a boon for healthcare organizations. Eliminating vulnerabilities and threat opportunities makes it easier to avoid risky situations in the future.
Avoiding Cyberattacks as a Healthcare Provider
There’s no easy way to avoid bad actors in 2024. Attempting to eliminate all risk is not only stressful, but virtually impossible from a practical point of view.
Thankfully, perfection is not required to maintain a safe and successful healthcare practice.
Conclusion
The modern provider would do well to consider:
- Building payer connections with redundant payer systems
- Establishing robust security protocols and performing annual security audits
- Upping the ante with data retention policies, particularly with third-party vendors
So how do healthcare organizations take action today?
By planning ahead with flexibility and foresight.
The organizations least impacted by cyberattacks will be those that prioritize both redundancy and resiliency.
Source: Orbit Healthcare







 WebProNews is an iEntry Publication
WebProNews is an iEntry Publication